The Changing Motives Behind Cybercrime
Symantec warns in a report published yesterday (July 8) that a new group of criminal hackers — dubbed the “Morpho” group — is driven by quick financial gains, attacking multibillion-dollar companies such as Twitter, Facebook, Apple and Microsoft, which have all publicly acknowledged the attacks.
Morpho has infiltrated 49 major corporations in 20 different countries to steal valuable intellectual property. In 2013, they targeted legal firms then moved on to financial, pharmaceutical, commodities and telecommunications companies, reports Voice of America. Morpho has managed to access emails, legal policy documents, financial records, product descriptions and training documents.
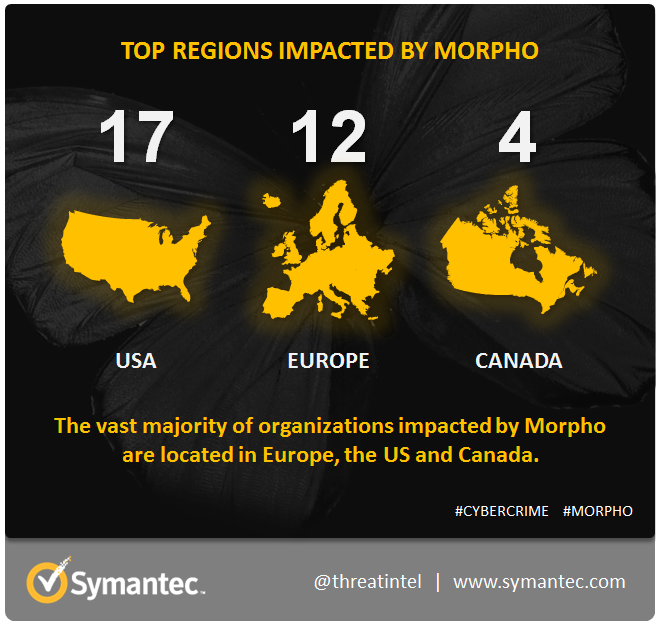
On its blog, Symantec explains, “Morpho is a disciplined, technically capable group with a high level of operational security. Having managed to increase its level of activity over the past three years whilst maintaining a low profile, the group poses a threat that ought to be taken seriously by corporations.” Symantec believes the group is “agnostic about the nationality of its targets” so is probably not backed by any country. As seen on the map above, a third of the cyberattacks were on companies based in the U.S.; Europe and Canada came in second and third.
“A key difference between attacks coming from competitors and state-sponsored attackers is that competitors are likely in a better position to request the theft of specific information of value and make more rapid use of this information than government-sponsored attackers would,” the report concludes.
Symantec knows that the group writes its malicious code in English, naming its encryption keys based on American pop culture and gaming, The New York Times reports. Morpho works during U.S. working hours (maybe because that’s when targets are most active) and has a lot of resources to develop their hacking tools to break into both Windows and Apple computers. Morpho has even managed to use one zero-day vulnerability.
Researchers traced Morpho’s activities back to March 2013 and believe that they are still active today — one of its latest attacks took place in June 2015 in the Central Asian offices of a global law firm. They are exceptionally good at covering up their tracks, renting servers using bitcoin, the anonymous cryptocurrency.
“We know that their ‘op sec’ is very, very good,” said Vikram Thakur, a senior manager of the attack investigations team at Symantec, using the shorthand for “operational security.” “Who they are? We don’t know. They are virtually impossible to track,” he said to NYT.
CyberEdge Group’s research published in March shows that 2014 brought new levels of cybersecurity attacks, despite an increase in IT security spending. In fact, a majority of IT departments expect to be breached in some capacity or another in the next year. Seventy-one percent of respondents had their networks breached in 2014, an increase from 62 percent the year prior. Twenty-two percent of respondents reported being attacked at least six times in 2014. Of those surveyed, 52 percent believe another attack will hit in the coming year.
[vc_row full_width=”” parallax=”” parallax_image=””][vc_column width=”1/1″][/vc_column][/vc_row][vc_row full_width=”” parallax=”” parallax_image=””][vc_column width=”1/1″][vc_separator color=”grey” align=”align_center” style=”” border_width=”” el_width=””][vc_single_image image=”148412″ alignment=”center” style=”vc_box_shadow_3d” border_color=”grey” img_link_large=”” img_link_target=”_blank” css_animation=”left-to-right” img_size=”full” link=”http://pymnts-com-develop.go-vip.net/whats-hot-today/”][vc_column_text css_animation=””]
To check out what else is HOT in the world of payments, click here.
[/vc_column_text][vc_separator color=”grey” align=”align_center” style=”” border_width=”” el_width=””][/vc_column][/vc_row]